Subdomain scanners and finders are critical to any penetration test and should always be used because they enumerate the targets for you. Before any hack or pentest you have to know what to aim at first. V3n0m is an open source tool used for scanning and finding subdomains, scanning web application vulnerabilities including SQL injection, Cross Site Scripting (XSS), Remote Code Execution (RCE), and Local File Inclusion (LFI) bugs.
The tool can exploit the vulnerabilities found during the scanning process. V3n0m scanner also features DNS Bruteforcer, Cloudflare resolver, Vulnerable FTP scanner, and Admin pages finder utilities. The DNS Bruteforcer module enumerates the DNS record of all the subdomains associated with the target web application.
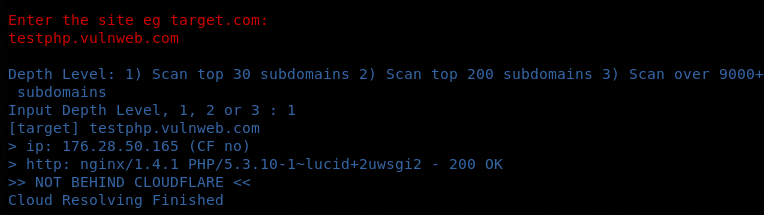
Cloudflare resolver checks if the target web application is using the Cloudflare services as a security measures. Cloudflare provides internet security, resistance against Distributed Denial of Services (DDoS) attack, Content Delivery Network (CDN), and distributed domain name server services to the web application clients. Dorking is another important feature of V3n0m scanner. V3n0m Dorker can take on up to 500 threads and 100 pages per dork to explore search engines for the vulnerable web pages. The tool can also verify the vulnerabilities of the crawled web pages.
How to Install V3n0m Scanner
V3n0m is a Python tool that requires Python3 to operate. To install V3n0m scanner, first clone the repository from Github as shown below.
git clone https://github.com/v3n0m-Scanner/V3n0M-Scanner.git
After cloning the tool, navigate to the tool’s directory and execute the setup.py file to complete the installation process. The following commands install V3n0m subdomain scanner and the required dependencies automatically.
cd V3n0M-Scannerpython3 setup.py install --user
How V3n0m Subdomain Scanner and Finder Works
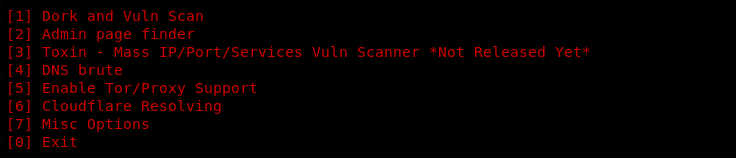
In order to run V3n0m scanner, navigate to the src folder in the tool’s directory. The folder contains v3n0m.py file. Running v3n0m.py file using the following command in the terminal opens the scanner menu as shown in the following screenshot.
Python3 v3n0m.py
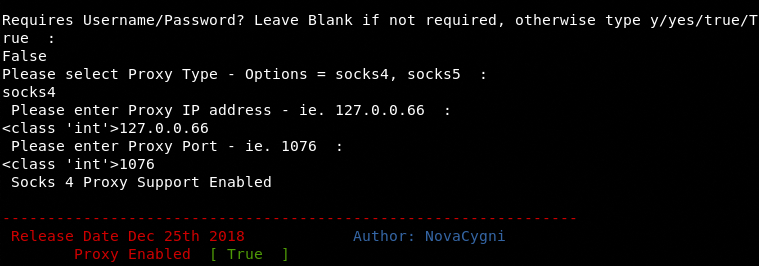
The menu contains all the scanning and exploitation modules (utilities), each having a sequence number. Each module can be selected by typing its sequence number in the command line. There is a proxy setup option (at #5) in the menu. The option allows proxy enabling to secure the scanning process. The following screenshot shows different configuration options to enable the proxy.
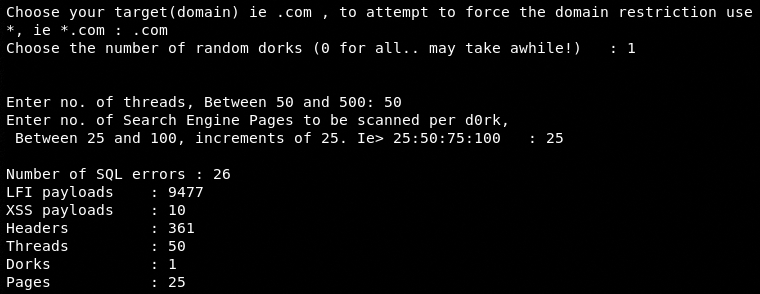
The first option in the menu is the V3n0m Dorker. When we select the Dorker, the tool asks for the domain extension, the number of dorks, threads, and number of search engine pages to be scanned per dork.
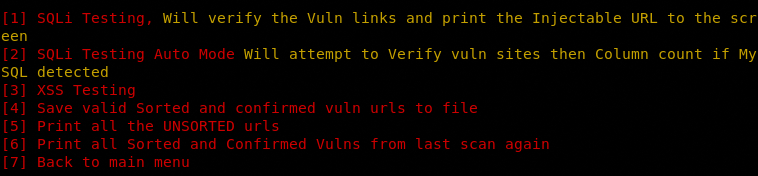
In the next step, select the type of vulnerability that must be present in the web pages to be fetched by the tool. The current Dorker version of the tool supports SQLi and XSS vulnerabilities. Once the required input values are provided to the tool, it compiles the list of web pages containing the desired vulnerabilities. The Dorker module can also validate the vulnerabilities by using the payloads defined for this purpose.
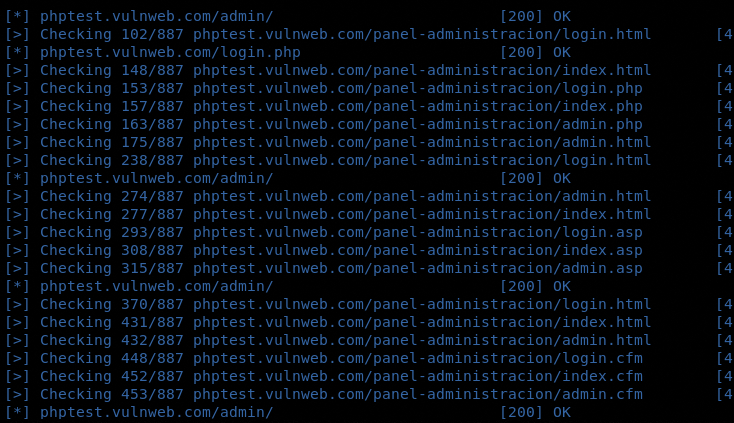
We can use other modules (utilities) listed in the menu by following the similar pattern. The admin page finder option can find all the login form pages in the target web application.
The Cloudflare option can check if the target web application is using the Cloudflare services.
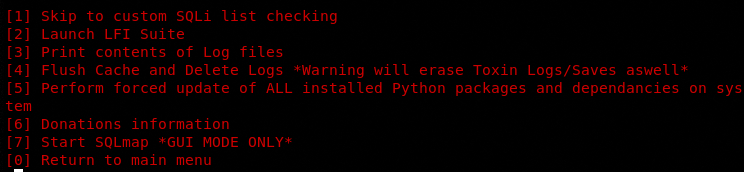
The “Misc options” in the menu contains LFI and SQL scanning modules. The following screenshot shows all the features of this section.
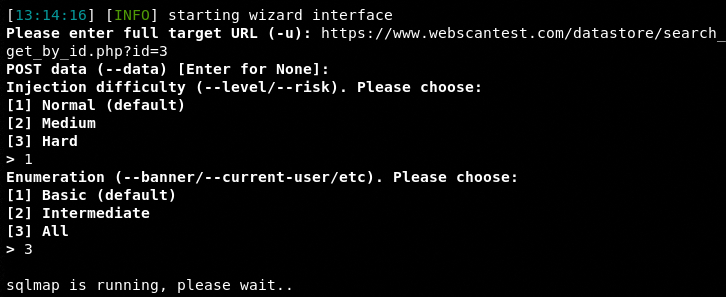
The SQL module uses SQLmap (GUI mode) to automate the scanning and exploitation process. By selecting the SQL scanner option from the list, the tool invokes SQLmap. Configure the SQLmap by providing the target web application address, scan level, and enumeration options.
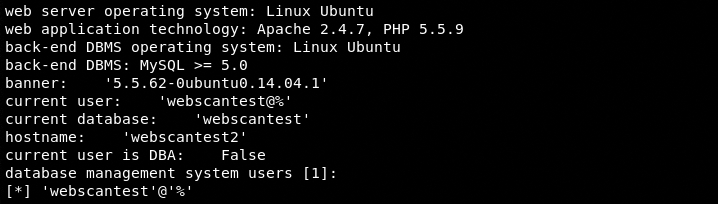
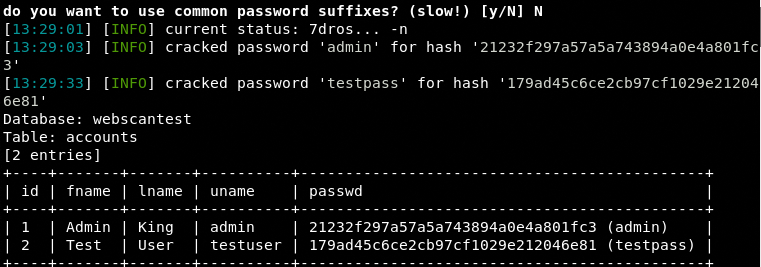
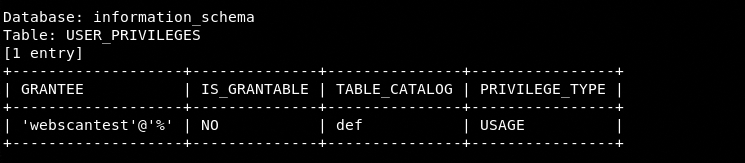
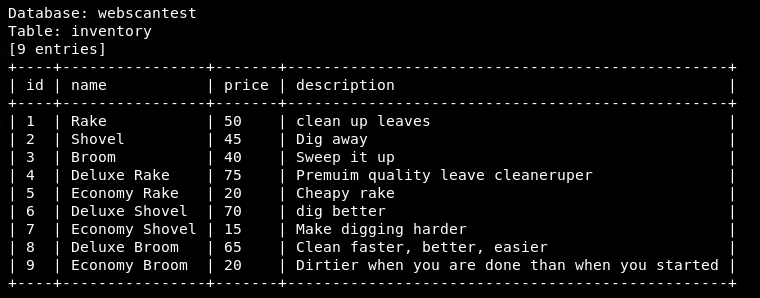
Once SQLmap is configured, it starts scanning the target web application. If the target web application is vulnerable to database injection, the tool explores the Backend Database Management System (BDMS) and fetches results as shown in the following screenshots.
BDMS
Accounts Table with Cracked Passwords
User Privileges Table
Inventory Table
Similarly, we can use the LFI scanner by following the on-screen instructions to scan and exploit the LFI vulnerabilities in the target web applications.
Conclusion
Subdomain scanners are incredibly helpful and the V3n0m scanner is a handy tool having dorking, scanning, and exploitation features. The tool can be used for scanning as well as attacking the web applications during penetration testing.