Nikto and Nmap are two widely used penetration testing tools. Nikto is a web scanner whereas the Nmap is known as a network mapping tool. In this tutorial, we shall cover both tools in detail to understand the basic functionalities along with the unique and overlapping features of both tools.
Nikto Tool Overview
Nikto is a web server scanning tool that is designed to perform various information gathering and vulnerabilities assessment tasks, such as collecting servers information, finding software misconfigurations, classifying default files and programs running on a web server, detecting misconfigured or insecure files and programs, and identifying outdated web servers and programs. The scope of these scanning tasks is quite significant. According to Nikto’s official documentation, the tool is capable of identifying 6700 potentially dangerous files and programs running over 270 servers with 1250 versions.
Important Features
Nikto has many features supporting its basic functionalities. Some interesting features of the tool are listed below.
- SSL support for Unix and Windows OS
- HTTP proxy support
- Multiple ports and servers scanning
- Multiple output file formats
- Encoding techniques (for IDS evasion)
- Mutation techniques for fishing
- Custom scanning options
- False-positive reducing techniques
- Credentials guessing for authorization
How to Install Nikto Tool?
Nikto is a pearl based scanner that is supported by almost all major operating systems. Linux users can install the tool by simply typing the following command.
sudo apt install nikto
The docker method requires the following commands to install the tool.
git clone https://github.com/sullo/nikto.git cd nikto docker build -t sullo/nikto . docker run --rm sullo/nikto
We can also download and unpack the latest package from the following Nikto release page. However, the requirements (Perl, Perl Modules, OpenSSL, LibWhisker) must be manually installed to use the unpacked version of the tool.
https://github.com/sullo/nikto/releases tar -xvfz nikto-2.16.tar.gz
[Note: Replace the <nikto-2.16.tar.gz> according to the latest version available at the release page]
How Nikto Works?
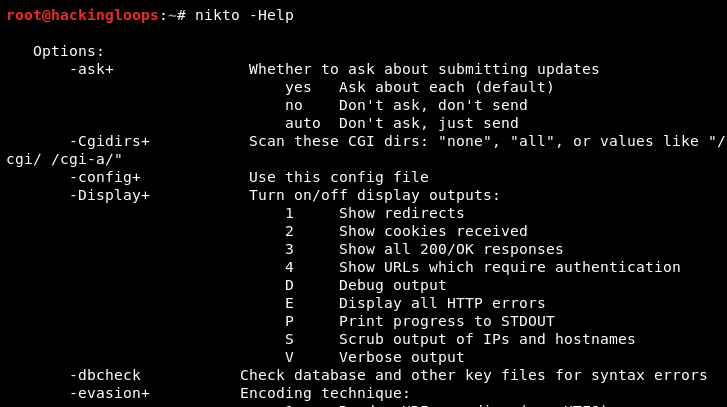
Nikto has a simple command-line interface to run the scanner utilities. The help command displays all the available options and parameters that can be used to start the scanning process.
nikto -Help
Following is the default Nikto usage command (without any specific options or parameters) to initiate the scanning.
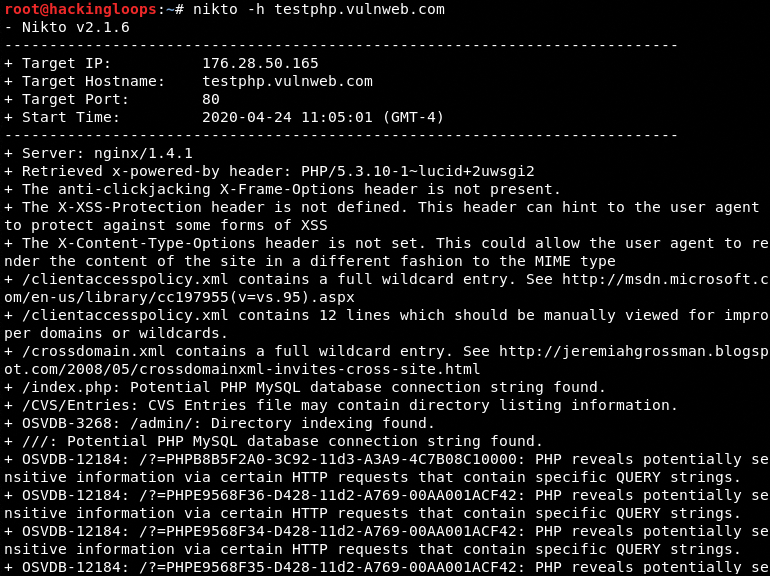
nikto -h <target server>
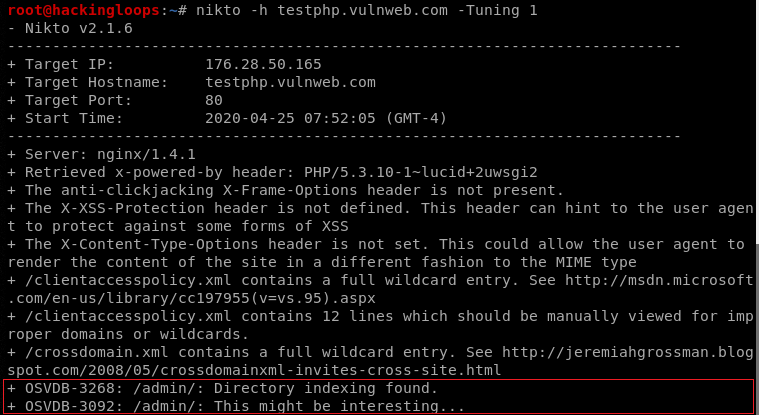
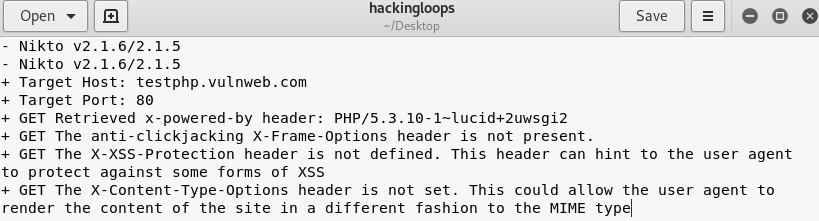
The screenshot shows server information and different vulnerabilities found during the default scanning process. Although the basic usage command gives detailed information about target servers and vulnerabilities, we can refine the scanning process by utilizing the available parameters mentioned in the Help section of the tool. The following section presents the core parameters, highlighting the advanced features of the Nikto tool.
A) Tunning Options
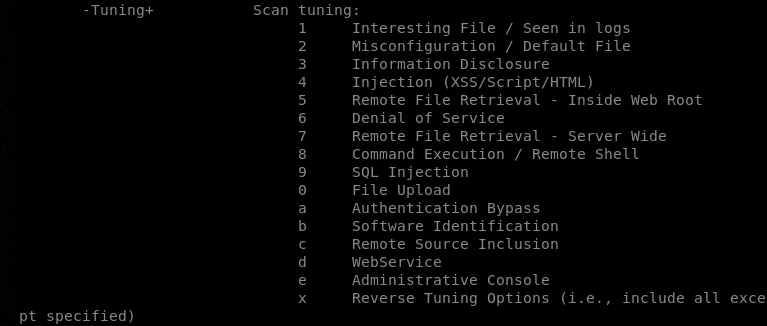
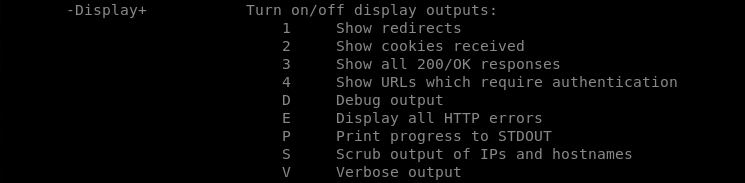
The following screenshot shows the available tuning options supported by the Nikto tool.
The tuning option allows the scanning of specific vulnerabilities (or information) instead of all the potential vulnerabilities (or information) covered by the Nikto scanner. The tuning option can be utilized in the following format.
nikto -h <target server> -Tuning <tuning sequence number> #OR nikto -h <target server> -T <tuning sequence number>
For instance, we can tune the Nikto tool to find interesting files at the target web server by mentioning its sequence number in the following format.
nikto -h testphp.vulnweb.com -Tuning 1
B) Display Options
We can expand the display feature during the scanning process by utilizing the following parameters.
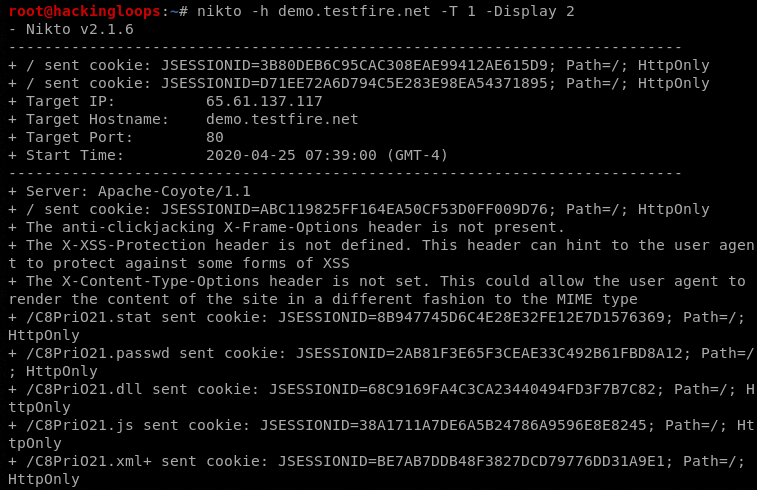
For example, we can display cookies information on the screen during the scanning process using the following command format.
nikto -h demo.testfire.net -T 1 -Display 2
C) Plugin Options
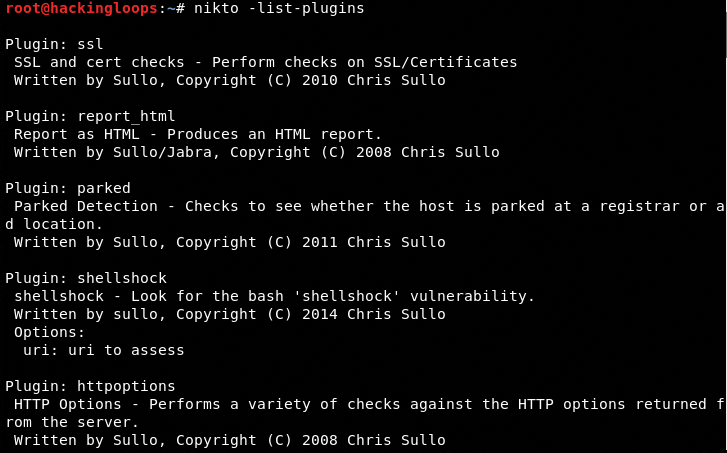
Nikto tool has a decent list of plugins that can be found by typing the following command in the terminal.
nikto -list-plugins
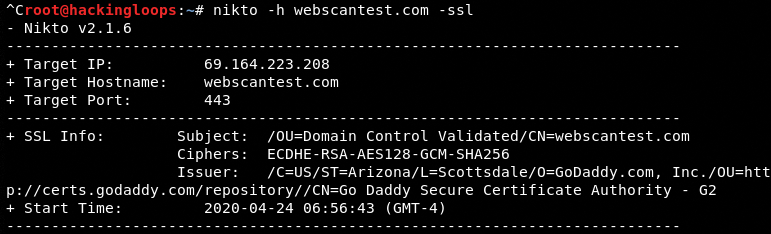
Each plugin has a different role. For example, we can use the –ssl plugin to gather SSL/Certificates information about the target web server using the following command.
nikto -h webscantest.com -ssl
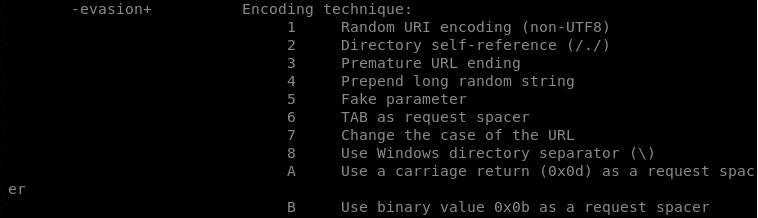
D) Evasion Techniques
Encoding is one of the useful Nikto features to bypass the defense system of the target hosts. Nikto tool supports the following evasion (encoding) techniques that can be used by introducing the -evasion parameter followed by the evasion method in the command line.
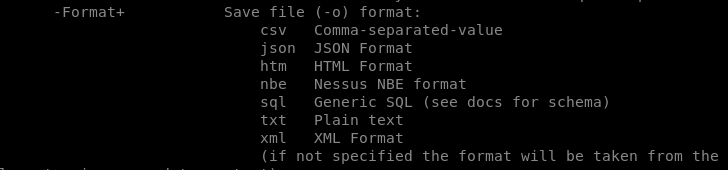
E) File Format Options
Nikto tool allows the storage of scanning results in the following formats.
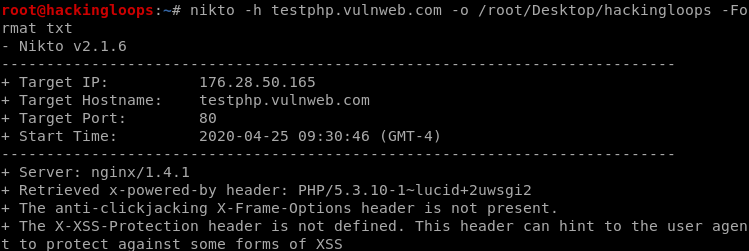
For example, we can store the results in a file called hackingloops in text format using the following command.
nikto -h testphp.vulnweb.com -o /root/Desktop/hackingloops -Format txt
The above command creates a hackingloops.txt format result file at /root/Desktop location.
Nikto Limitations
Since Nikto assesses a large number of files, programs, and servers, the tool uses the techniques that should fetch results in the shortest possible time. This approach makes Nikto unstealthy and obvious in log files or Intrusion Detection Systems (IDS) of target hosts. The tool does offer some anti-IDS technique with no guarantee.
Nmap Tool Overview
Nmap is a network mapper that is used for network discovery and auditing tasks. The core tasks performed by the tool include live network hosts discovery, finding different services running on each host, banner grabbing, and gathering information about firewalls and packet filtering systems used by the target networks. Besides network mapping, Nmap has a scripting feature that is used to scan certain types of network vulnerabilities discussed in the later section of this tutorial.
How to Install Nmap?
Some Linux operating systems may allow Nmap installation through the following single command.
sudo apt-get install nmap -y
There is a more reliable Nmap installation process that involves Nmap package cloning and running the setup commands as discussed below.
First of all, clone the Nmap source package from Github using the following command.
git clone https://github.com/nmap/nmap.git
In the next step, navigate to the package directory and run the following configuration command in order to verify the availability of all the libraries required by the Nmap tool.
./configure
If no errors are detected during the configuration check, run the following command as a final step to complete the installation process.
make && make install
The Nmap installation and version can be verified through the following command.
nmap --version
How Nmap Works?
Following is a default Nmap command used to scan a host, range of hosts, or a target network.
nmap <target IP | range of IP addresses | host name | Network>
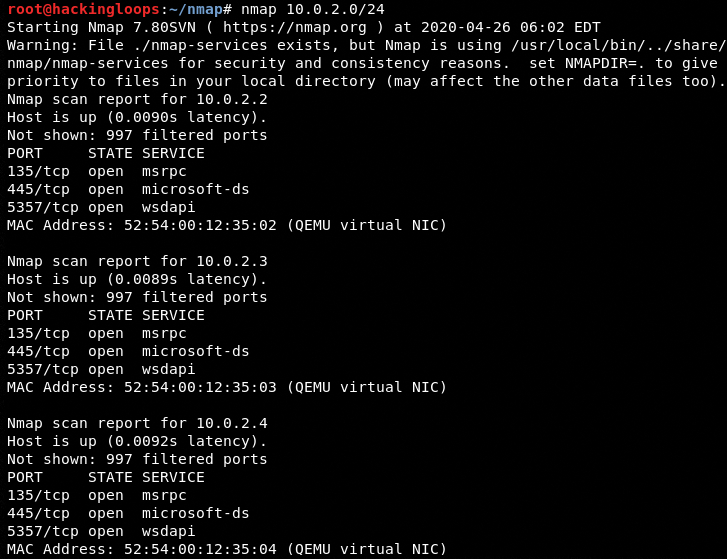
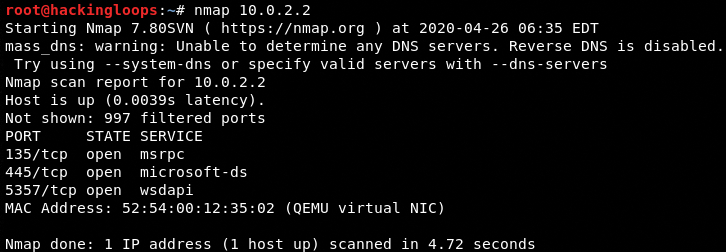
The following screenshot shows the scan results performed on a test network (10.0.2.0/24)
nmap 10.0.2.0/24
The screenshot shows some valuable information about live hosts in the network, such as their IP addresses, MAC addresses, open ports, and running services. The available information is helpful in target enumeration and other penetration testing phases. The main features of Nmap can be explored in the help section by typing the nmap in the command line terminal.
nmap
Following is a brief overview of the core functionalities of Nmap mentioned in the help section.
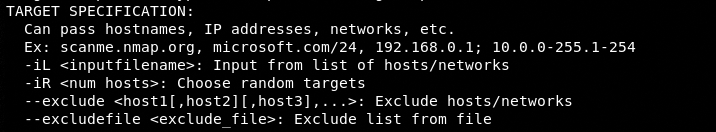
A) Target Specification
The following screenshot shows different ways we can use to specify the target.
For example, we can specify the IP address of the target machine to initialize Nmap scanning.
nmap 10.0.2.2
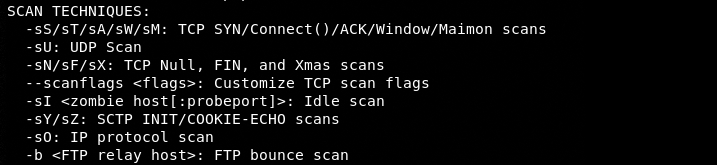
B) Scan Techniques
Nmap supports all the major network probing techniques, such as TCP, FIN, NULL, and XMAS scan. The following screenshot shows different scan techniques that can be used by mentioning the respective flags in the command.
For example, we can use the TCP scan by mentioning the -sN parameter in the command.
nmap -sN 192.168.10.1
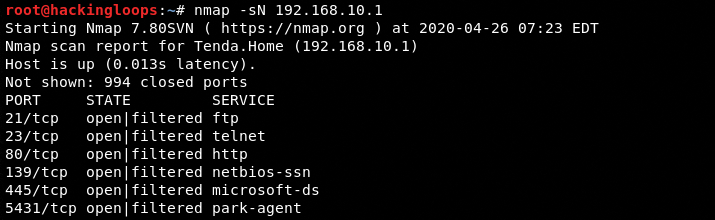
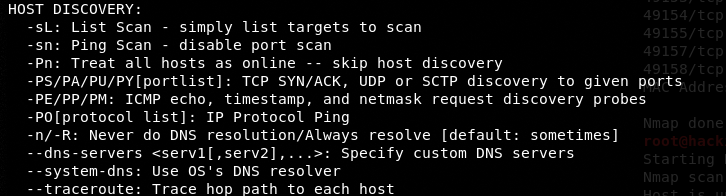
C) Host Discovery Options
Nmap has the following variety of host discovery options that can be used to customize the scanning process.
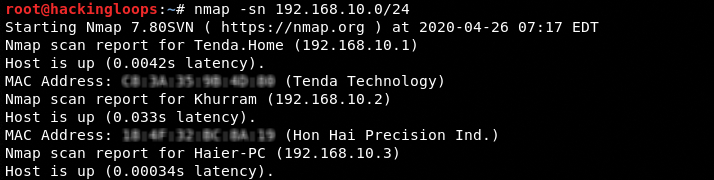
For instance, we can use the ping scanning (-sn) option to skip ports’ information and display only live hosts in the scan results.
nmap -sn 192.168.10.1/24
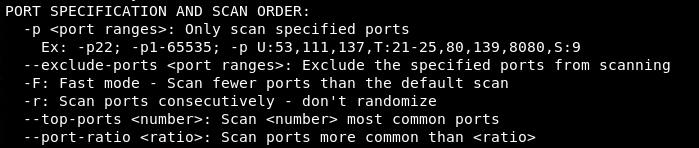
D) Ports Specification
Port specification is an important utility of the Nmap tool. The following specification options allow us to scan specific ports to finetune the attack strategy against target networks.
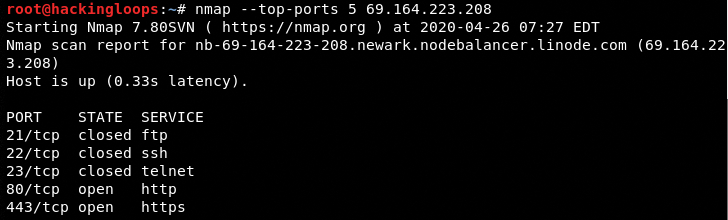
For example, we can specify the top five ports along with their status and services through the following command.
nmap --top ports 5 69.164.223.208
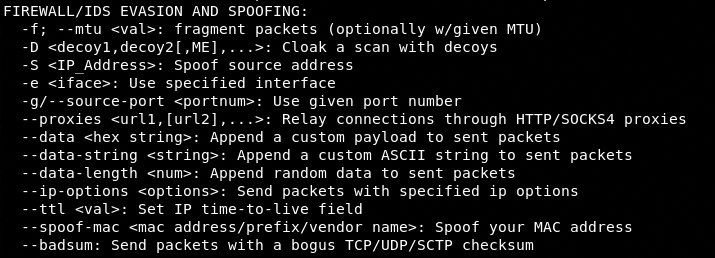
E) IDS Evasion and Spoofing
IDS evasion and spoofing is another useful Nmap feature. The evasion techniques mentioned in the following screenshot can be used to stay anonymous during the Nmap scanning.
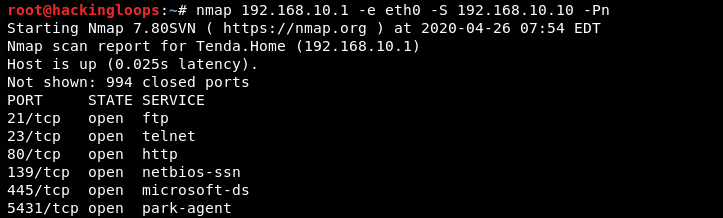
For example, we can spoof the source IP address in the following manner to manipulate the logs at the target host.
nmap 192.168.10.1 -e eth0 -S 192.168.10.10 -Pn
F) Nmap Scripting Engine (Vulnerabilities Scanner)
The Nmap Scripting Engine (NSE) is probably the less talked about but the most exciting feature of the Nmap tool. The NSE allows running different NSE supported scripts to find out different types of software vulnerabilities in local or remote target hosts. The following screenshot shows different ways we can mention scripts in the commands to initiate the vulnerabilities scanning process.
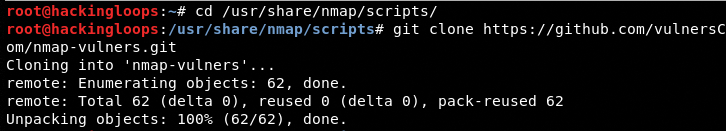
The NSE also allows integration of third-party scripts to test the target host for a variety of Common Vulnerabilities and Exposure (CVE). For instance, we can integrate the Vulners NSE script with Nmap scripts using the following command.
git clone https://github.com/vulnersCom/nmap-vulners.git
[Note: select the script must be cloned in /nmap/scripts/ to be picked up by NSE]
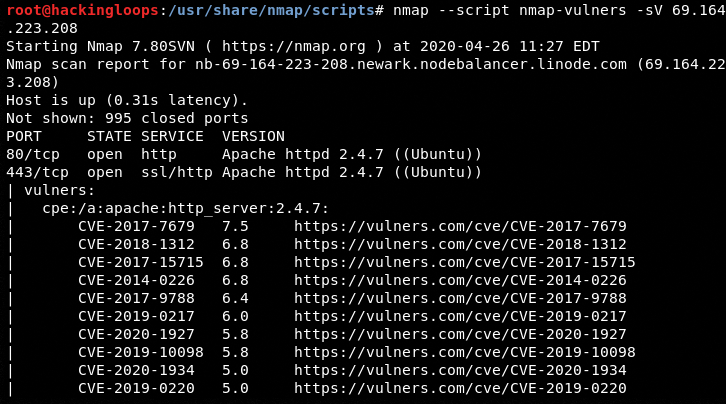
The following command is a demonstration of NSE vulnerability scanning against a remote target.
nmap --script nmap-vulners -sV 69.164.223.208
The NSE results can be seen in the following screenshot where a number of CVE’s are detected by Nmap.
Conclusion
Nikto and Nmap are two diverse penetration testing tools. Nikto is used to assess web servers’ vulnerabilities whereas Nmap is used to discover live hosts in target networks. Both tools also share some common attributes. Nikto gathers useful information similar to Nmap banner grabbing before assessing the vulnerabilities in target servers. The Nmap has a strong NSE feature that can discover a variety of software vulnerabilities in target hosts similar to the Nikto tool.